Everything You Need to Know About Agentic Identity
Jan 8, 2026
Executive TL;DR
With AI agents on the rise, every IAM and security stakeholder must understand that agentic identities aren’t just non-human identities (NHIs) with better automation. They’re ambitious actors who never stop working.
The core shift: risk shows up in the sequence of actions over time, not in any single login, token, or entitlement change.
To govern agents, IAM needs visibility into decision loops and delegation chains, not just credentials.
Old identity assumptions no longer hold
Most IAM programs were built around a clean divide:
Humans authenticate, receive entitlements, and operate within organizational norms and limits.
Non-human identities execute narrowly defined workloads with permissions scoped in advance.
Agentic identities fit neither category because they:
Are persistent decision-makers
Plan, adapt, and act across multiple steps
Decide what to do next, which systems to touch, and which tools to use based on goals and context
Act without waiting for explicit instructions at each turn
That changes what “identity” looks like in practice. Identity does not show up as a single event. It unfolds as behavior, delegation, and a chain of access decisions that change while the agent operates.
Why this breaks traditional IAM
Traditional IAM secures moments in time, such as logins, role assignments, and token issuance. That works when access attempts are made by humans at human speed, or are machine-driven and tightly scoped.
Agents operate between those moments. They decompose goals into steps and discover and request access as they go. One permission unlocks the next. Each request can look reasonable alone, but risk lives in the sequence.
And the security problem often begins after access is granted. With long-running agents, credentials rotate, but intent persists.
What agentic identities are, and what they’re not
Agentic AI systems may comprise a single agent or multiple agents operating in coordination to achieve an outcome. These agents determine paths, tools, and systems to use, and then act on those decisions without continuous human oversight.
That autonomy changes how identity behaves. Unlike traditional NHIs, agentic identities change as agents reason, adapt, and interact with different parts of the enterprise environment.
Agentic identities are
Goal-driven decision loops that keep operating until an objective is met
Cross-system actors that express identity through actions, not just a single credential
Delegation-heavy workflows that often operate through chains of service accounts, roles, tokens, and tools
Agentic identities are not
Just “smarter bots” running a fixed script
A single service account or workload identity you can understand in isolation
Automatically low-risk because credentials are short-lived
How agents consume access in practice
Agents don’t approach a goal by requesting every permission upfront. They break the goal into steps. Each step reveals which tools, permissions, or data they need next, so access is discovered rather than predefined.
Traditional models grant access first and assume that usage comes later. Agents often reverse that flow. They attempt an action, learn what’s missing, and acquire the next layer of access.
Micro-example (how compounding happens):
Agent starts with read-only analytics access
It hits a limit and requests config-read access to diagnose the issue
It determines a change is needed and requests write access in one system
It delegates the fix to a deployment identity that has broader privileges
Each step can look reasonable alone. The chain is the risk.
Tool connections can create implicit privilege
Many agents do not authenticate to tools using OAuth tied to the current user. Instead, they use long-lived secrets, API keys, tokens, or service credentials configured in the workflow or agent environment.
This can create a mismatch between who is allowed to run the agent and what the agent can do. A user may have limited direct access to an application, but by running an agent that already has a permanent credential configured, they can trigger actions they should not be able to perform.
From the outside, it still looks like normal tool usage. The risk is that the permissions are effectively inherited through configuration, not granted through an approval process tied to the user and the moment.
Why short-lived credentials don’t eliminate identity risk
Short-lived credentials reduce exposure, but they don’t remove accountability gaps.
Agents rely on temporary tokens, delegated credentials, and role sessions. Tokens expire and sessions rotate, but an agent’s intent persists. As one credential ends, another replaces it.
IAM records separate events tied to different identities, but in reality, it is one actor continuing the same reasoning. The question becomes how access combines across identities to reach an outcome. Without that connection, accountability breaks and intent is invisible.
Delegation chains are where context disappears
Delegation is how agents operate at scale, and it’s where visibility erodes fastest.
Agents work through chains of delegation: impersonating service accounts, exchanging API tokens, and federating into workload identities. Each handoff can be valid. Each hop can behave as designed.
The problem is context loss. Most IAM systems record these as separate events. A role assumption here. A token exchange there. What they miss is the sequence that connects them. Without that thread, identity becomes fragmented execution instead of a single decision-maker spanning systems.
Security teams then reconstruct behavior after the fact, inferring intent from logs never meant to explain it.
What this looks like in a real enterprise
Agent permissions in the enterprise can look ordinary until viewed collectively.
Scenario 1: “Fix the performance issue”
An agent detects a performance issue with limited analytics access, assumes a diagnostic role, identifies a configuration problem, and fixes it using a separate deployment identity.
IAM logs each step under a unique identity. None appears risky alone. The real identity is the agent coordinating the entire sequence.
Scenario 2: “Prepare a report”
An agent is asked to prepare a quarterly report. It pulls metrics from a BI tool, then discovers it needs customer fields from a CRM. A developer previously connected the CRM using a long-lived API secret so the agent can “just work.” The agent exports the dataset to a collaboration tool to share with stakeholders.
Each system sees a legitimate action. The risk is the combined outcome: sensitive data moved across systems using credentials that are not tied to the user running the agent, through a chain no single control point evaluated end-to-end.
This is why agentic identities are easy to underestimate. Their behavior only makes sense in the context of a continuous decision loop.
Start here this week
If you do nothing else, start by making agentic identity visible and governable in the places where risk concentrates.
Start here checklist:
Inventory where agents already operate (workflows, platforms, SaaS copilots, internal tools)
Identify which identities they execute through (service accounts, roles, tokens, workload identities)
Inventory agent tool connections and how they authenticate (OAuth vs long-lived secrets)
Identify run-context mismatches (who can run an agent vs what its configured credentials allow it to do)
Flag high-impact actions (IAM changes, data exports, production deploys, privilege grants)
Define guardrails for those actions (allowed tools, allowed targets, approval requirements)
Require traceability through delegation chains (correlate hops back to the originating agent or workflow)
This is foundational. You cannot govern what you cannot map.
How risk scales in agentic environments
Agentic identities accumulate risk faster because access is discovered, chained, and delegated across systems and identities.
Compounding access creates sideways expansion
Privilege expansion becomes autonomous when agents optimize for task completion unless guardrails restrict decision scope.
This can begin with narrow permissions. As the task develops, those permissions unlock the need for additional access. The expansion is not always a single obvious escalation. It can be accumulation across tools and identities.
Least privilege cannot be treated as a one-time entitlement decision. For agents, it has to be enforced continuously for high-impact actions, and evaluated in the context of the decision loop.
Coordination multiplies visibility gaps
Multi-agent coordination multiplies risk because identity context fractures as tasks are delegated across many agents.
Agents collaborate to complete complex workflows. One analyzes data, another diagnoses infrastructure, and a third applies changes. Each may operate under different identities, tools, or domains.
Everything can look normal to individual systems. What disappears is the thread connecting actions into one decision flow. Fragmented visibility lets risk spread even when no single agent appears over-privileged.
Misuse scenarios that matter
New scenarios show up when influence becomes as important as direct access:
An agent nudges another agent to execute a privileged action, and each individual step appears legitimate.
An agent splits actions across systems so no single log stream looks suspicious, but the combined outcome is harmful.
These are identity problems because they depend on delegation paths, chains of authorization, and missing end-to-end context.
Why audits and investigations struggle
Audits struggle because execution is easier to record than reasoning.
Logs capture events. They rarely capture why decisions were made or how actions connect across systems. Traditional IAM trails flatten behavior into isolated entries, forcing teams to infer intent after the fact.
In practice, the hardest investigations involve tool connections. If an agent used a stored secret, the audit trail often shows the tool identity, not the human who triggered the run, and not the full chain of connected systems. This is why correlation across the full flow matters, not just collecting more logs.
In an agentic world, accountability depends on connecting:
the originating objective
the chain of identities used
the sequence of actions
the final outcome
Without that, you can have “complete” logs and still have incomplete answers.
How to explain agentic identity internally
Agentic identity is hard to govern if teams can’t describe it consistently.
One-minute explanation for executives
Agents behave like autonomous digital workers. They can be fast and independent, but risk comes from decision speed multiplied by visibility gaps. IAM must connect intent and execution so you can understand what the agent was trying to do, what identities it used, and what it changed.
Explanation for architects and engineers
Agentic identity works in a loop:
An agent forms intent
It discovers missing access
It executes through an identity (often an NHI)
It produces an outcome
The loop repeats until the objective is met
Governance has to follow that loop. Visibility, boundaries, and traceability need to apply across steps, not just at login.
Misconceptions to stop repeating
Short-lived credentials don’t automatically mean low risk when intent persists.
Agents aren’t just smarter bots. They’re decision-makers operating across systems.
When behavior drives access, risk shows up in the chain, not a single event.
Agents are not just NHIs.
What this means for your IAM program
The rise of agentic identity necessitates a new approach.
Treat decision sequences as first-class security objects, not just entitlements.
Correlate actions across tokens, roles, and NHIs back to the originating agent or workflow.
Define guardrails for what decisions agents can make as context changes, especially for high-impact actions.
This allows autonomy and delegation to be treated as identity behaviors that require supervision and traceability.
Conclusion
Agentic identities change the shape of identity risk. The biggest shift is not that agents authenticate differently. It is that they operate continuously, discover access as they go, and act through delegation chains that fragment context.
If IAM continues to govern only logins, roles, and tokens in isolation, it will miss the behavior that matters. The path to control starts with visibility into where agents run, what identities they use, and how multi-step decisions connect to outcomes.
Agent discovery with Linx: visibility with context
Linx provides Agentic Identity Discovery and Governance to close that gap, and give teams a single platform to security and govern human, non-human, and agentic identities.
Along with your human and non-human identities, you can discover which agents are in use, who has access to them (humans or other agents), and what those agents have access to.
Who is allowed to run an agent vs what the agent can reach
Agents often carry permanent access through long-lived secrets and pre-wired tool connections. Linx helps you see mismatches between who can execute or influence an agent and what the agent’s configured credentials allow it to do. This makes implicit privilege visible so teams can remediate it.
Agent to app flow mapping across connected tools
Developers connect agents to many apps quickly, often through generic HTTP and API components or custom connectors. Linx correlates agent activity into an end-to-end flow from agent to application to resource. This helps teams understand blast radius, spot unexpected connections, and investigate multi-step behavior without stitching evidence together manually.
Which agents exist and who owns them?
Get an inventory of agents and quickly flag ones without clear owners.

Who can access the agent?
You can see which accounts have access to an agent, which helps you understand who can run it, manage it, or influence its behavior.
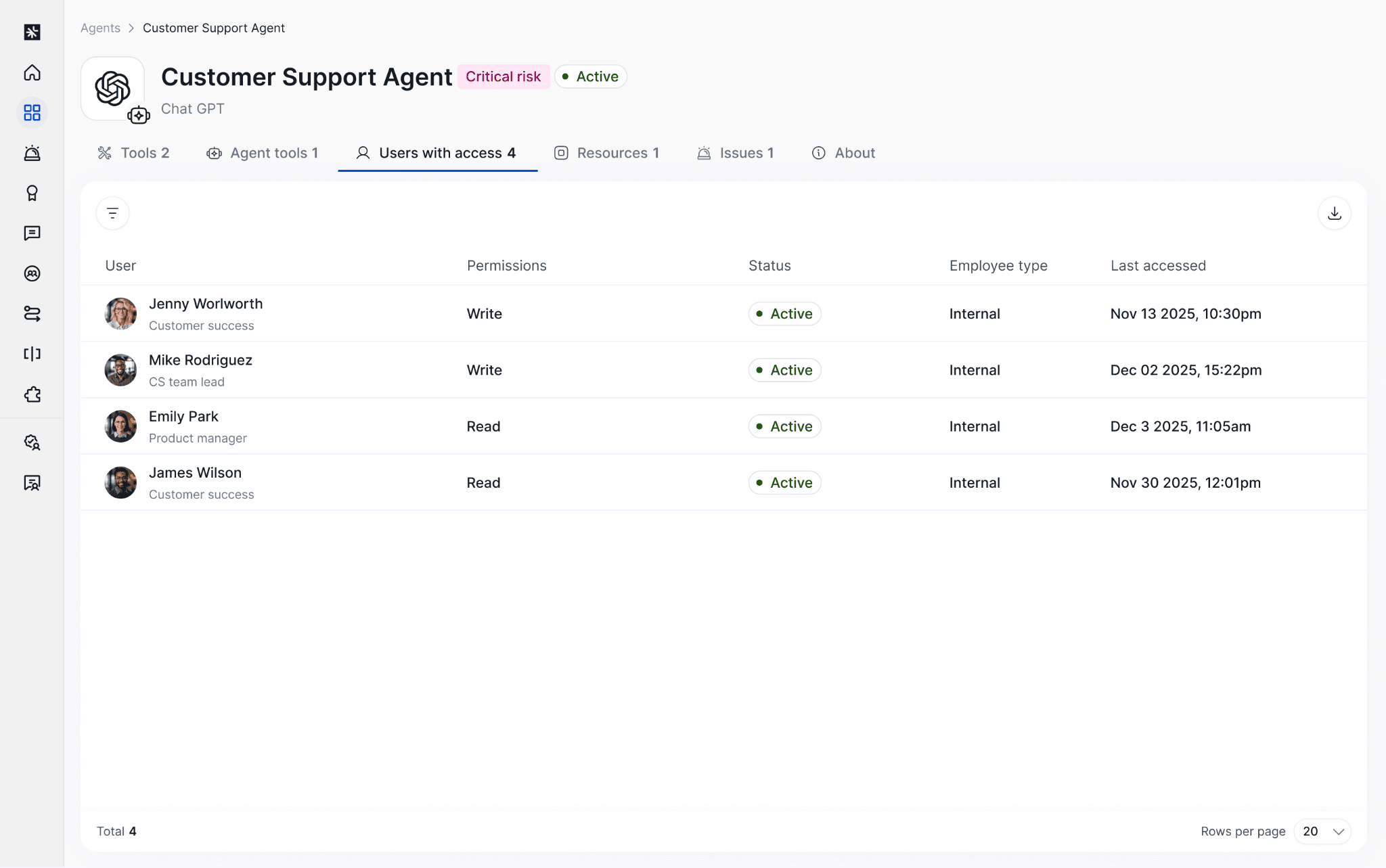
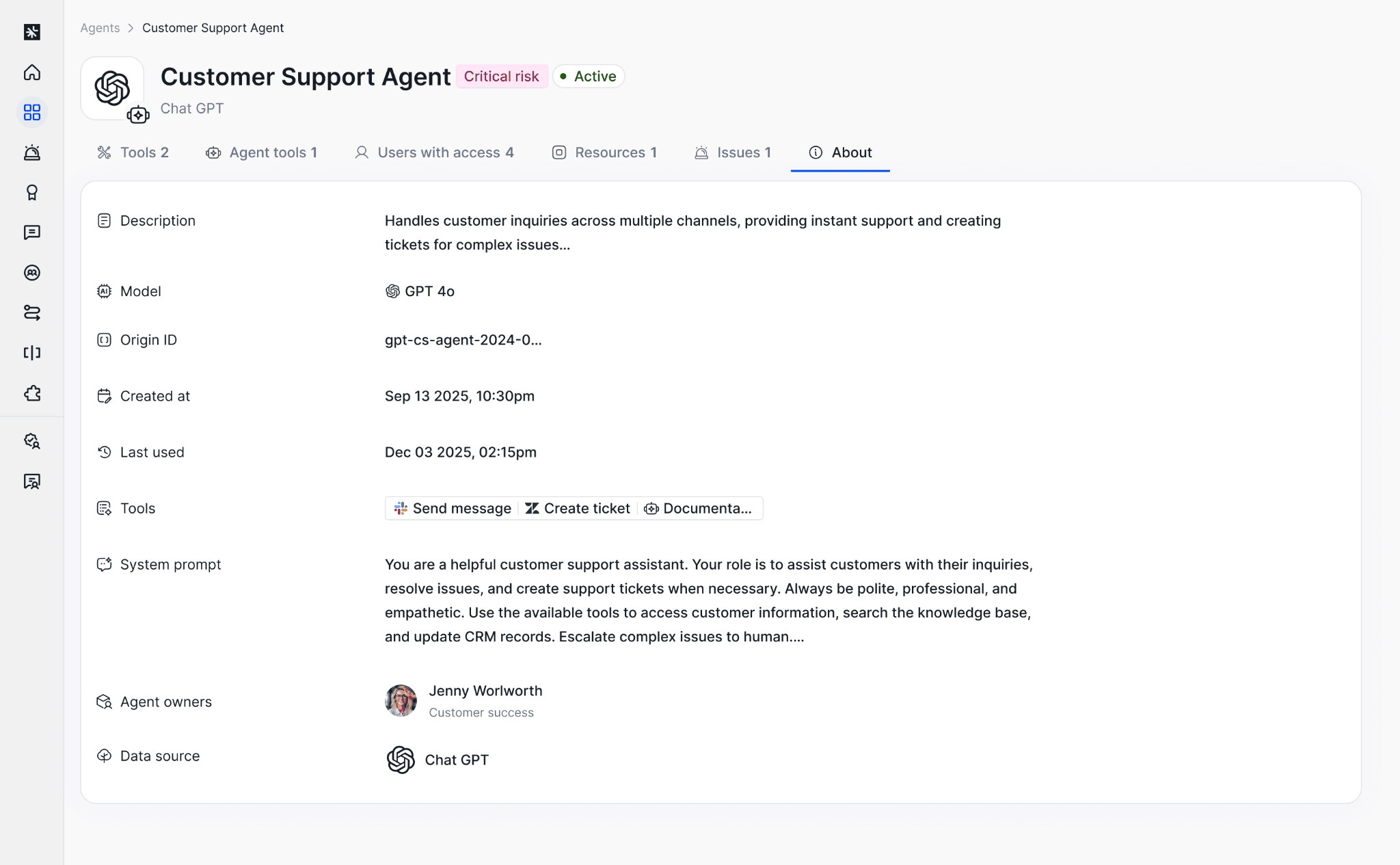
What does the agent have access to?
You can review the permissions and resources the agent can reach, including signals that help you prioritize what to look at first, and how the agent got the access in the first place (API token, service account, OAuth, etc.).
Bring agentic identities into your existing governance program
Most IAM teams already have a set of routines that work: access reviews, ownership assignment, least privilege, and remediation. Linx incorporates agentic identities into the same platform you use to secure and govern human and non-human identities across SaaS, cloud, and on-prem applications. That keeps visibility and governance consistent, even as identity types expand.












